A quickly expanding botnet called Chaos is targeting and infecting Windows and Linux devices to use them for cryptomining and launching DDoS attacks.
This Go-based malware can also infect various architectures, including x86, x86-64, AMD64, MIPS, MIPS64, ARMv5-ARMv8, AArch64, and PowerPC, used by a wide range of devices from small office/home office routers and enterprise servers.
Even though it mainly propagates by attacking devices unpatched against various security vulnerabilities and SSH brute-forcing, Chaos will also use stolen SSH keys to hijack more devices.
It also backdoors hijacked devices by establishing a reverse shell that will allow the attackers to reconnect at any time for further exploitation.
While analyzing around 100 samples discovered in the wild, security researchers Danny Adamitis, Steve Rudd, and Stephanie Walkenshaw at Lumen’s Black Lotus Labs found that Chaos is written in Chinese and uses China-based command-and-control (C2) infrastructure.
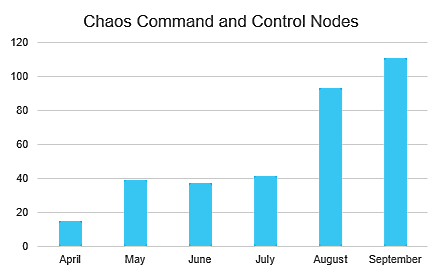
They also found that the botnet is targeting an extensive array of industries and has expanded exponentially since it was first spotted in April.
“Using Lumen global network visibility, Black Lotus Labs enumerated the C2s and targets of several distinct Chaos clusters, including a successful compromise of a GitLab server and a spate of recent DDoS attacks targeting the gaming, financial services and technology, and media and entertainment industries – as well as DDoS-as-a-service providers and a cryptocurrency exchange,” the researchers said.
“While the botnet infrastructure today is comparatively smaller than some of the leading DDoS malware families, Chaos has demonstrated rapid growth in the last few months.”
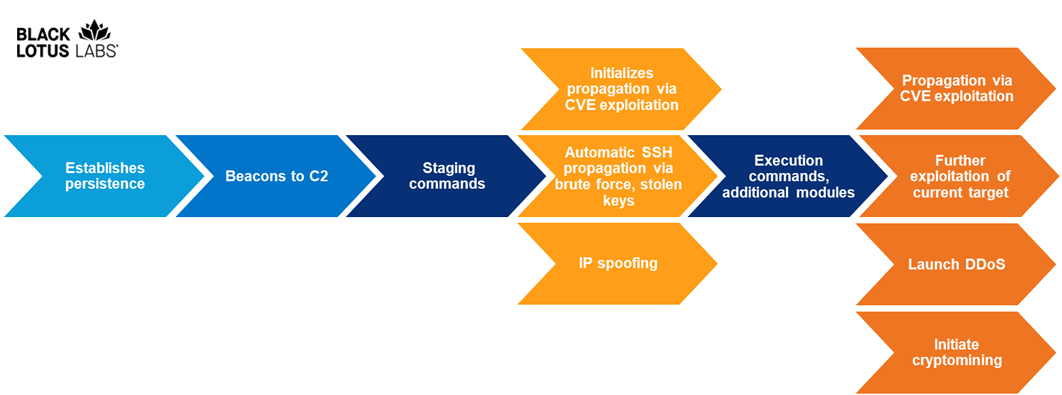
After the botnet successfully takes over a device, it will establish persistence and reach out to its C2 server, which sends back staging commands prompting the malware to propagate further, start mining for cryptocurrency, or launch a DDoS attack.
Black Lotus Labs researchers added that some bots had been seen receiving dozens of commands over just a few days (more than 70 in some cases).
The botnet focuses on European targets, but the bots are spread almost everywhere, with hotspots in the Americas and the Asia Pacific. The only exceptions are Australia and New Zealand, where no Chaos bots have been detected so far.
Chaos seems to be using building blocks and capabilities from another botnet known as Kaiji, a malware also capable of cryptomining, launching DDoS attacks, and establishing reverse shells on infected devices.
“Based upon our analysis of the functions within the more than 100 samples we analyzed for this report, we assess Chaos is the next iteration of the Kaiji botnet,” they added.
“Kaiji was originally discovered in 2020, targeting Linux-based AMD and i386 servers by leveraging SSH brute forcing to infect new bots and then launch DDoS attacks.”
Black Lotus Labs says it has null-routed all Chaos C2 servers on Lumen’s global backbone to block them from sending or receiving data from infected devices.
Network defenders are advised to monitor for Chaos infections and connections to suspicious servers using indicators of compromise shared on GitHub and to keep their systems patched against newly disclosed security vulnerabilities the malware might start targeting.
Remote workers and router owners should install security updates and patches as soon as possible and change default passwords on all their devices.
“While the shift to Go-based malware has been underway for the last few years, there are few strains that demonstrate the breadth of Chaos in terms of the wide array of architectures and operating systems it was designed to infect,” they concluded.
“Not only does it target enterprise and large organizations but also devices and systems that aren’t routinely monitored as part of an enterprise security model, such as SOHO routers and FreeBSD OS.
“And with a significant evolution from its predecessor, Chaos is achieving rapid growth since the first documented evidence of it in the wild.”
Is your business affected by cybercrime?
If you encounter a cybercrime or cyberattack, you need to act quickly. Cyber crime in its various formats such as online identity theft, financial fraud, stalking, bullying, hacking, email fraud, email spoofing, billing fraud, email scam, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disaster. Contact Digitpol’s hotlines or respond to us online.

You must be logged in to post a comment.