Emotet Attacks Continue to Soar as Botnet Spreads Globally
The number of attacks related to Emotet continue to spike after the dangerous botnet re-emerged over the summer with a fresh phishing and spam campaign that is primarily infecting devices with a banking Trojan, according to new research from HP-Bromium.
See Also: Webinar | Mainframe Security For Today's Crazy World!
During the third quarter of 2020, the number of Emotet infections increased 1,200% compared to the second quarter of the year, according to an analysis by HP-Bromium. After a nearly six-month hiatus, an uptick in spam and phishing emails related to the malware began in mid-July, the security researchers say (see: Emotet Botnet Returns After Months-Long Hiatus).
This increase in activity was also spotted by other researchers who note that Emotet is increasingly used to deliver a banking Trojan called QBot or QakBot to infected devices. This malware is primarily designed to steal banking data and credentials and is known to target the customers of several large financial institutions, including JPMorgan Chase, Citibank, Bank of America, Citizens, Capital One and Wells Fargo (see: Update: Emotet Botnet Delivering Qbot Banking Trojan).
Besides the banking Trojan, Alex Holland, senior malware analyst at HP-Bromium, notes that Emotet infections are usually the precursor to a ransomware attack.
"The typical pattern of Emotet campaigns we have seen since 2018 suggests that we are likely to see weekly spam runs until early 2021," Holland says. "The targeting of enterprises is consistent with the objectives of Emotet's operators, many of whom are keen to broker access to compromised systems to ransomware actors."
The U.S. Cybersecurity and Infrastructure Security Agency has called Emotet one of the most dangerous malware variants currently active (see: CISA Warns of Emotet Attacks Against Government Agencies).
Worldwide Infections
Since July, the malspam campaign that is spreading the Emotet botnet has been spotted in the U.S., U.K., Canada, Austria, Germany, Brazil, Italy and Spain, according to previous research by security firm Proofpoint. CISA has noted that its own intrusion detection system that monitors federal civilian networks, has detected approximately 16,000 alerts related to the Emotet since the botnet re-emerged.
The HP-Bromium research finds the Japan and Australia have sustained the most Emotet infections between July and September.
The report also confirms that Emotet is spreading through a social-engineering technique called thread-jacking, where the botnet operator replies to stolen email threads as a way to lure victims into opening malicious content since it appears to come from a trusted source.
The HP-Bromium report also notes that Emotet is spreading through spam or phishing emails that usually contain a malicious attached document. If opened, the file enables malicious macros that install the malware within the compromised device. Some of these documents are designed to look like invoices and purchase orders.
"In one campaign, we saw hackers encrypting malicious documents with Microsoft Word's 'Encrypt with Password' feature, to slip past network security and detection tools," Holland says. "The malware, in this case, TrickBot, would only deploy if the user entered a password sent with the phishing email. This meant that most anti-virus tools weren't able to access the file to scan it, but we were able to watch it in the micro-virtual machine. It may sound like a relatively simple tactic, but it's one that has proven to be effective in bypassing detection."
Emotet and Qakbot
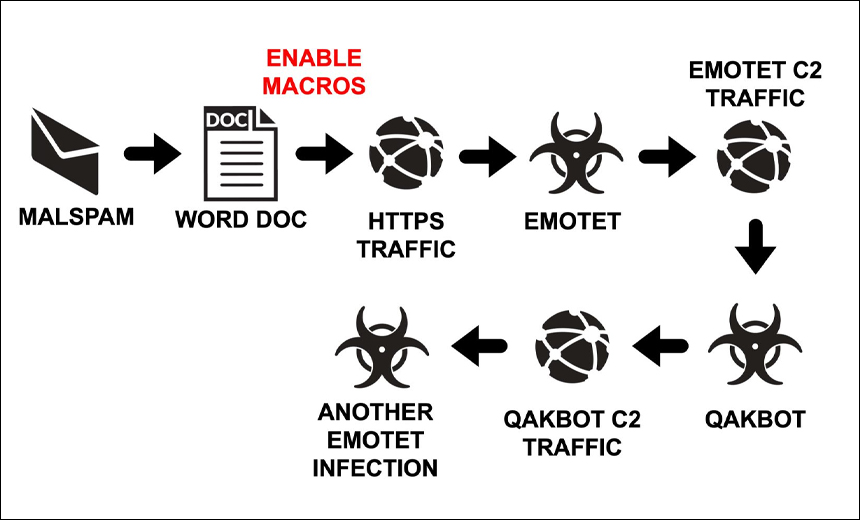
Over the past weekend, Bradley Duncan, a threat researcher, posted a blog on the SANS Technology Institute website that found that not only will Emotet infect a device with the Qakbot Trojan, but that Qakbot will then turn around and attempt to spread another Emotet infection, which helps grow the size of the botnet.
Recommendations
The HP-Bromium research notes that best defense against Emotet is implementing an email content filtering policy to reduce the risk of compromise by encrypted attachments containing the malware. The report also suggests organizations implement DMARC, safe list attachments based on file types the organization would expect to receive and block encrypted attachments.
Is your business effected by Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Contact Digitpol's hotlines or respond to us online.
Digitpol is available 24/7.
Email: info@digitpol.com
Europe +31558448040
UK +44 20 8089 9944
ASIA +85239733884

You must be logged in to post a comment.