Bug Sweeping Service Benelux
Detection of spying or espionage equipment, Digitpol provides bug sweeping services to detect surveillance, spying and interception. Digitpol's team of experts provides the A to Z in detection of bugs, eavesdropping and espionage equipment. Spying devices and espionage equipment are easily available nowadays and the problem with commercial spying is rampant, Digitpol utilises military grade detection tools and will discover any form of bugging devices.
Tools We Use:
To conduct a TSCM search many different tools are required, the basics are the industry standard from REI such as FLIR, Oscar Red, Ocsar Green and we them on standby and ready.
- The Kestrel TSCM
- Predator RF Hunter 20 GHz Spectrum Analysis Kit
- REI OSCOR Blue & Green
- ORION HX NON LINEAR JUNCTION DETECTOR
- FLIR on tripod and handheld
- High grade spectrum analyzers (27ghz)
- WiFi and Bluetooth analyzers
- Monitoring of LAN networks for unauthorized traffic
- Analysis of VoIP services for unauthorized traffic
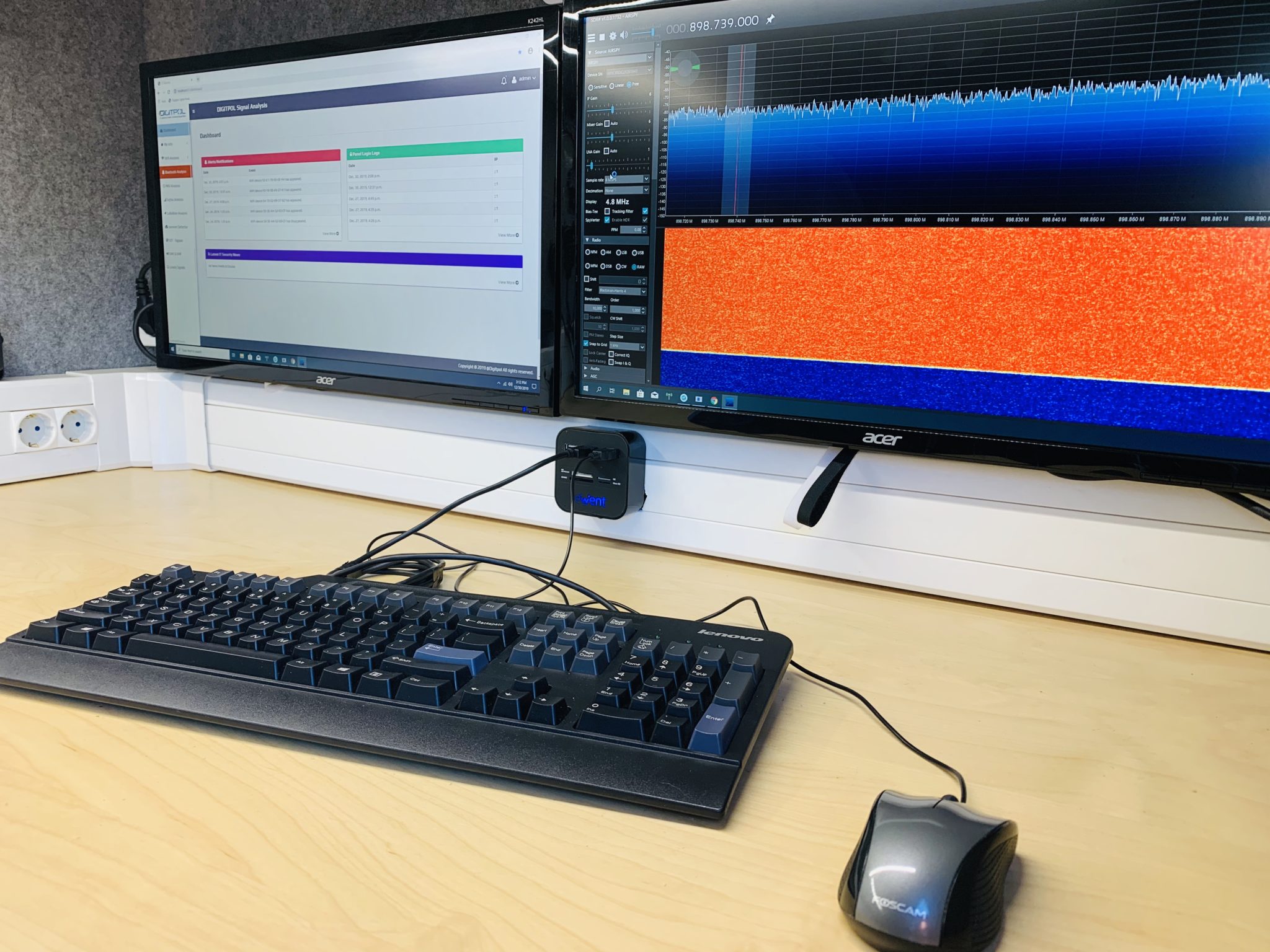
Sensor Based TSCM (Remote Monitoring)
Our sensor based TSCM module allows for monitoring in more locations with networking capabilities purpose built for remote and in-place spectrum monitoring. We can detect in real time new devices and prevent in real time listening equipment and active surveillance.
The TSCM tool set we deploy features a sweep rate of 28 GHz/s at 10 kHz RBW and 40 MHz IBW and advanced triggering capabilities, we can capture short duration or faint signals of interest with a higher probability. By conduct deeper analysis with patented software-defined spectrum analysis technology which enables wide bandwidths, deep dynamic range, and 9 kHz – 27 GHz frequency range.
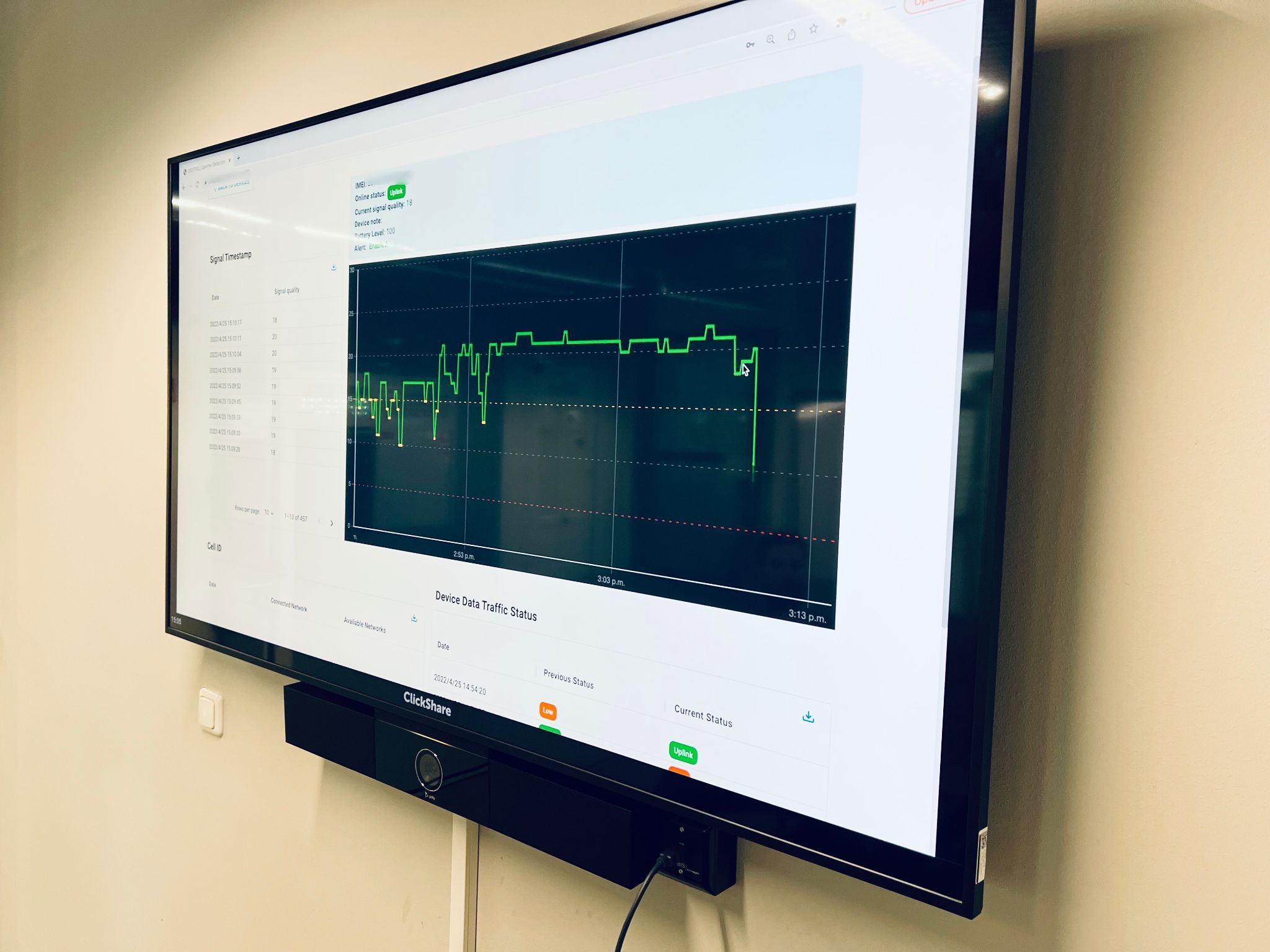
Detection of IMSI Catchers, Rogue Cell Sites & New Devices
This detection and monitoring module is a static wall or pole mounted device built to detect nearby jamming and to notify response teams in milliseconds of jamming events. The module named JamDetect can detect jamming, detect interference in the cellular network such as rogue base stations, detection of IMSI catchers and detection of new nearby devices. The platform contains a white list that enables the monitoring team to have a clear vision of known trusted nearby devices, cell towers and the rapid detection of new devices.
The JamDetect is the ultimate in the detection of espionage on a site from jamming to rogue activity, when used with several modules a mesh is created, this ensures a high level of security within the mesh. The Jammer Detector can alert responding or monitoring agents by SMS, email, API or in the portal.
Should I Be Concerned who’s on LAN or WiFi?
Are you concerned about information loss or business secrets being targeted over WiFI? A small amount of information could be worth millions to the right people or could damage important negotiations. Loss of confidential information such as executive schedules could even put lives in danger. Traditional physical security and cyber security are important, but there are many gaps they leave unprotected.
To ensure all is in order, a WiFi security sweep with a detailed report would provide an insight to any, technical surveillance issues.






Digitpol has been providing technical surveillance countermeasures security sweeps and eavesdropping detection services since 2013. We are based in The Netherlands but travel throughout the EU and the world for our clients. Our goal is to provide the highest standard of RF testing, TSCM, WiFi analysis and security services, information security and technical services for executive and corporate security. We are ready to respond immediately to your needs.
If someone or some company considers it is important enough to bug your home or your place of work, it is almost certain that they have considered monitoring your transport. If you drive anywhere or you are driven, it may be useful for someone to know your conversations whilst in your car. Bugs can be placed in a car without the need to enter the vehicle or have the keys; there are various ways to accomplish this.
Bugs placed in an office, lift, PC, clock, wall, lighting or under a vehicle.
With a sweep rate of 28 GHz/s at 10 kHz RBW and 40 MHz IBW and advanced triggering capabilities, we can capture short duration or faint signals of interest with a higher probability, using our network based sensors we can located instantly nre devices and detect digital bugging. Listening devices places in vehicles are more complex, a car is mobile and therefore can only be successfully bugged using a GSM bugging device that has no distance restrictions and the suspects would have global position (GPS) to monitor the car's position.
Most bugs fitted to vehicles are either fitted covertly inside or even under the vehicle itself. Modern cars are hard to gain access to without disturbing an alarm, so specialist vehicle bugs that often include a GPS covert tracker system are fitted underneath, or in the engine area where access can be gained comparatively easily. These bugs are small and unobtrusive with a short wire that can be fed through a drain hole or existing grommet that has a miniature microphone at the end.
The result being that a bug can be fitted to your vehicle in a matter of minutes that can record conversations inside the car, track the vehicles movements to within a few metres and yet entry to the car has not been necessary.
