Bug Sweeping Service Benelux
Detection of Spying and Espionage Equipment
Digitpol provides professional bug sweeping and counter‑surveillance services to detect and neutralize all forms of spying and surveillance. Our expert team offers comprehensive detection from identifying hidden microphones, cameras, and transmitters to uncovering digital espionage tools such as spying and stalkerware applications. We investigate both commercial and personal spying activities.
With the widespread availability of surveillance technology, the threat of unauthorized monitoring has become increasingly common. Digitpol employs military grade detection instruments and advanced forensic techniques to locate and identify any type of bugging or interception device. Our systematic approach ensures that all potential threats whether physical or digital are detected, providing our clients with complete confidence, privacy, and protection. Our service region is, all of The Netherlands, Brussels, Antwerp and Luxemburg.
Stalkware & Spying Apps
Digitpol specializes in mobile phone spyware detection and forensic analysis, providing in-depth investigations to identify and eliminate stalkerware or surveillance software. Our team of forensic experts utilizes advanced techniques, including live network packet monitoring, sector-by-sector file system analysis, and comprehensive digital forensics, to detect hidden tracking applications. We thoroughly examine mobile devices and wireless networks for any signs of unauthorized surveillance and provide a detailed technical report outlining our findings. This report can be used as evidentiary documentation in legal proceedings if necessary. If you suspect your device has been compromised, Digitpol's expert analysis ensures a thorough investigation, offering you security, privacy, and peace of mind.
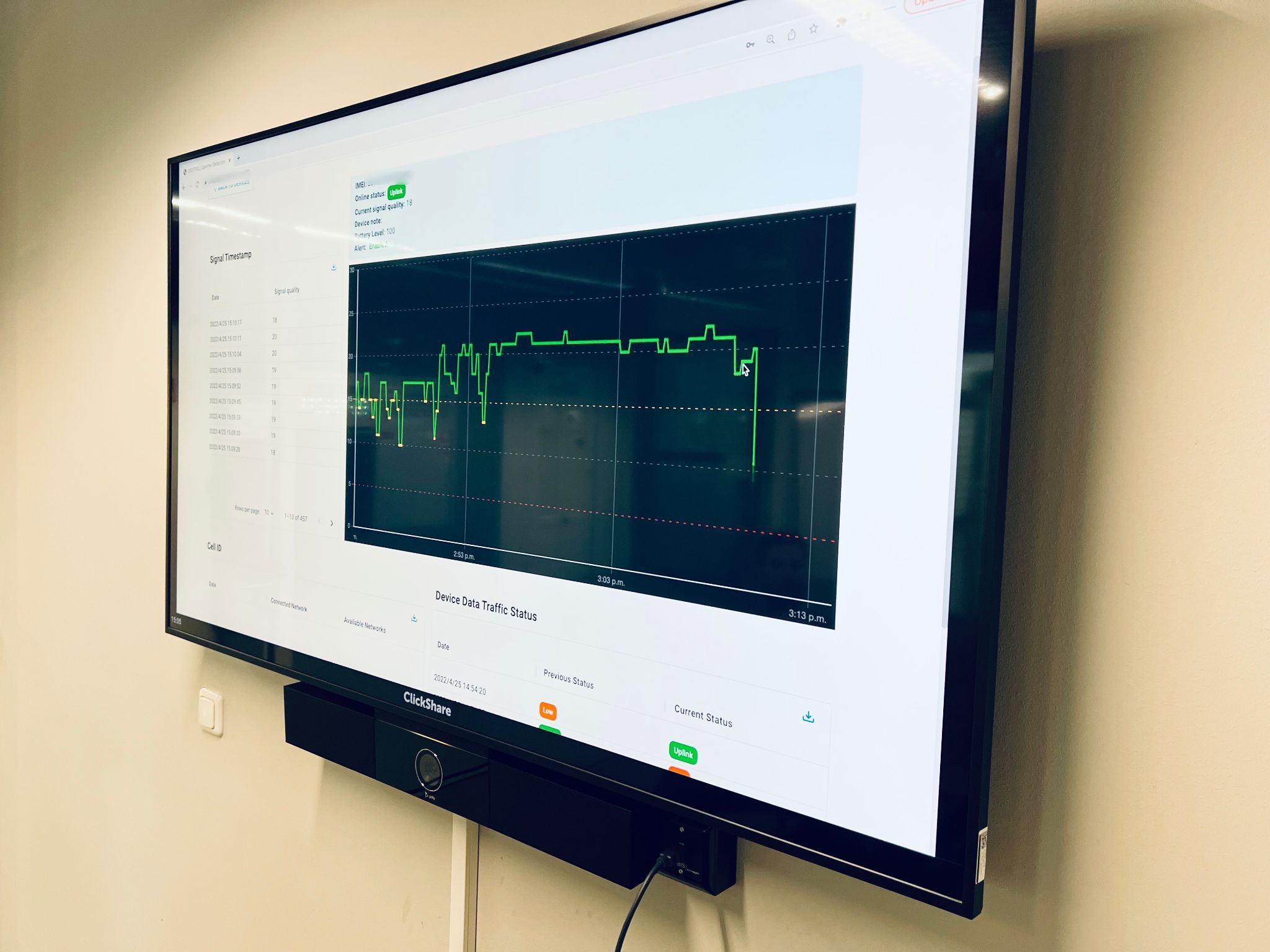
Detection of IMSI Catchers, Rogue Cell Sites & New Devices
Digitpol specializes in the detection and analysis of IMSI catchers, rogue cell sites, and unauthorized mobile interception devices that pose serious threats to privacy and communications security.
Our counter‑surveillance experts use custom tools to identify illegal cellular towers (cell site). We deploy active and passive Cell Site network mapping, and cellular protocol monitoring to identify anomalies in mobile networks that indicate the presence of fake base stations or interception equipment. These rogue devices often disguised as legitimate cellular towers can capture calls, messages, data, and subscriber identities without detection.
Should I Be Concerned About Who’s on My LAN or WiFi?
In today’s connected world, concerns about information theft or business secrets being targeted over WiFi are more relevant than ever. Even a small amount of sensitive information can be worth millions to the wrong people or could jeopardize critical negotiations. For example, the leak of executive schedules or confidential strategies could pose serious risks, including physical danger. While traditional physical security measures and cybersecurity protocols play vital roles, they often leave gaps in protection, particularly against covert surveillance.This process not only identifies vulnerabilities in your WiFi infrastructure but also detects spy cameras and other surveillance devices that might be intercepting sensitive data or monitoring your activities.



Tools We Use:
To conduct a TSCM search many different tools are required.
- The Kestrel TSCM
- Predator RF Hunter 20 GHz Spectrum Analysis Kit
- REI OSCOR Blue & Green
- ORION HX NON LINEAR JUNCTION DETECTOR
- FLIR on tripod and handheld
- High grade spectrum analyzers (27ghz)
- WiFi and Bluetooth analyzers
- Monitoring of LAN networks for unauthorized traffic
- Analysis of VoIP services for unauthorized traffic
