Wi-Fi Remote Hacking Pentest
Wi‑Fi Remote Hacking Pen Testing.
In today’s connected world, your public Wi‑Fi network can serve as a potential gateway for cyber attackers trying to breach your internal systems. Digitpol’s Wi‑Fi Remote Hacking Pentest simulates a real-world external attack targeting your public Wi‑Fi infrastructure, cloud management consoles, and associated systems. Our team identifies vulnerabilities in your Wi‑Fi configuration and cloud platforms that could allow unauthorized access or even lateral movement into your internal network. With a detailed, non‑disruptive assessment, we uncover weaknesses and provide actionable solutions to help you stay ahead of potential threats.
What We Test
Our service is usually carryout outside your business without providing us with any details, only the permission to test, we aim to test in a real life hacking scenario. We begin by assessing key components of your Wi‑Fi network and its connection to the cloud. Our testing focuses on several critical areas:
-
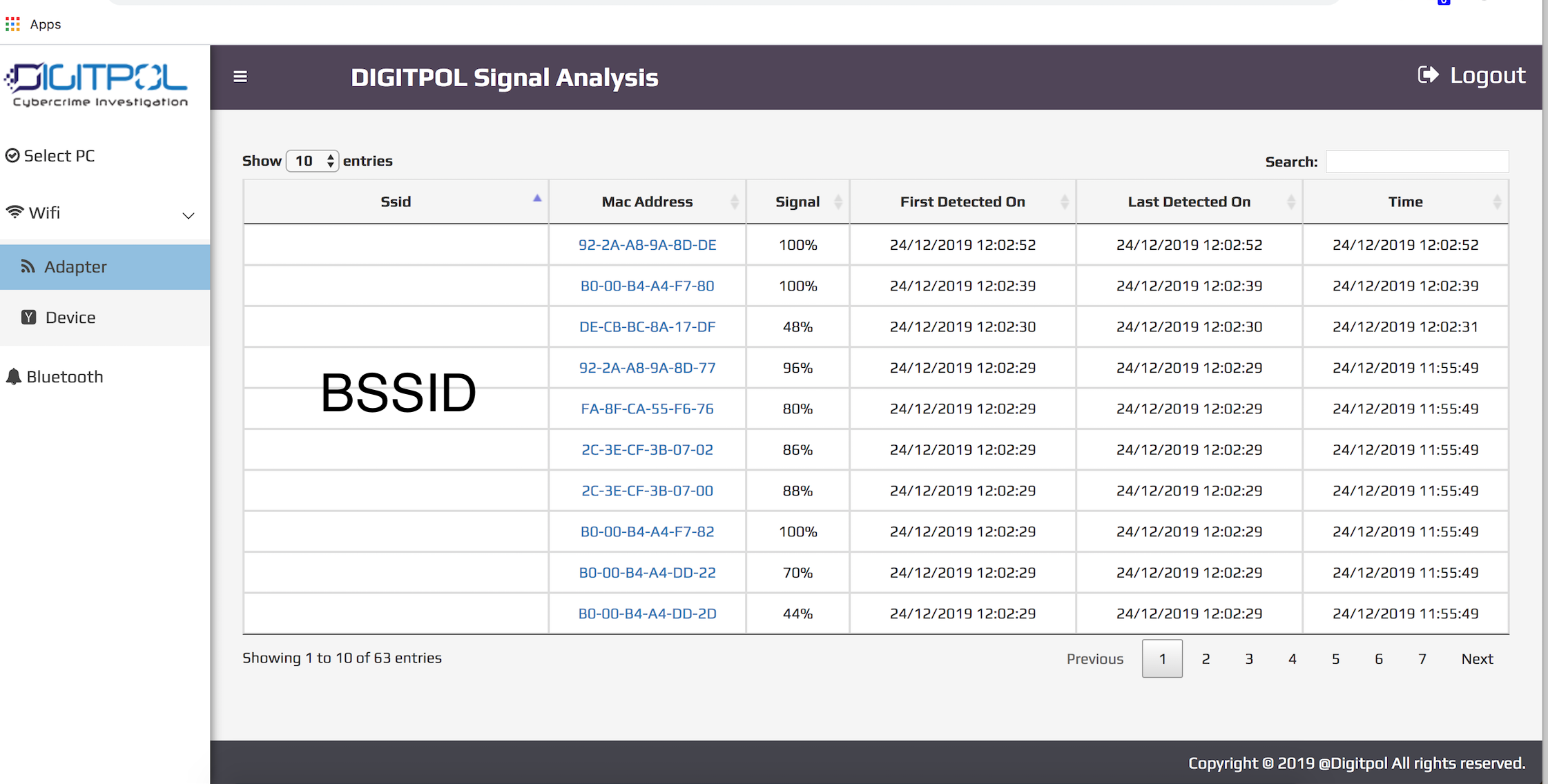
Public Wi‑Fi Management Interfaces: We identify any exposed cloud portals, controller access points, or SSH/HTTPS interfaces that may be accessible remotely by attackers.
-
Guest Network Segmentation: We test the security boundary between your public Wi‑Fi and internal systems to ensure proper isolation, preventing guests from bypassing network restrictions.
-
Authentication & Encryption: Our team reviews your Wi‑Fi authentication methods (such as WPA2, WPA3, and 802.1X) to ensure they’re securely configured to prevent unauthorized access.
-
Cloud Vendor Accounts: We assess whether your cloud management consoles are adequately protected with strong access controls, including multi-factor authentication (MFA).
-
Lateral Movement Potential: If vulnerabilities are discovered, we demonstrate how an attacker might move laterally into your internal systems, always keeping safety and caution at the forefront.
- Protected Wifi Networks: Once we have tested open networks, we will then start to gain access to protected wireless networks.
How It Works
Our pentesting process follows a systematic approach designed to ensure thorough, effective, and non‑disruptive testing:
-
Scoping & Authorization: We start by discussing your network and confirming the scope of the test. We then ensure that all necessary permissions are in place through a signed Rules of Engagement document before testing begins.
-
Discovery & Enumeration: We identify publicly available assets, such as public IPs, cloud services, and Wi‑Fi infrastructure, to determine what’s exposed to potential attackers.
-
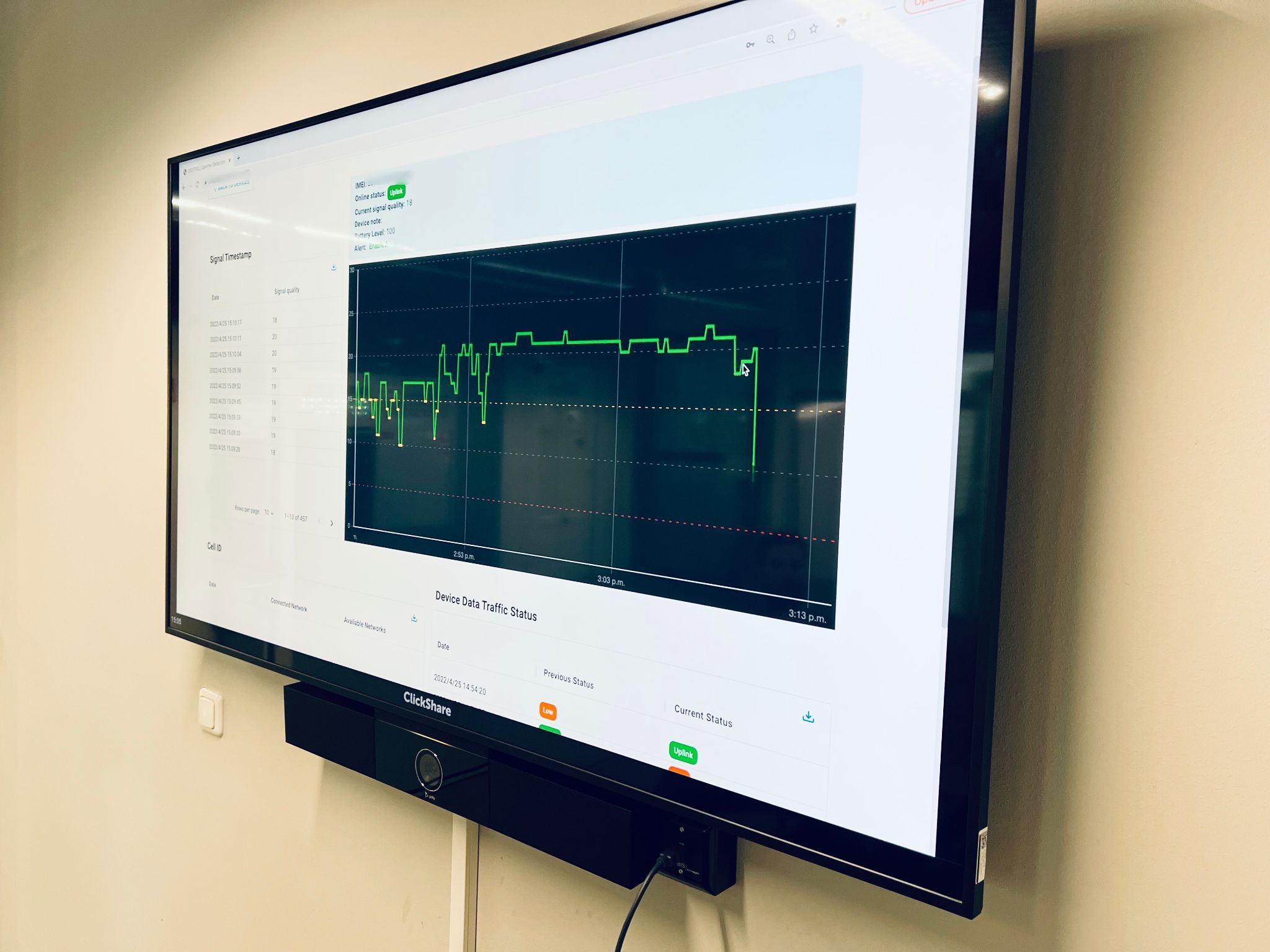
Vulnerability Assessment: Our team analyzes the configuration of your Wi‑Fi networks, guest network access points, and cloud systems for misconfigurations or flaws that could be exploited.
-
Controlled Exploitation: Using safe, non‑disruptive techniques, we simulate attacks to demonstrate how vulnerabilities can be exploited — typically showing proof-of-concept attacks like read-only configuration access or lateral movement.
-
Reporting & Remediation: After the test, we provide a comprehensive technical report, including detailed findings, risk analysis, and clear, prioritized remediation steps. We’ll also schedule a debrief to review the results and help guide next steps.
Why Choose Digitpol?
At Digitpol, we have extensive expertise in RF wireless security and a proven track record of identifying vulnerabilities in Wi‑Fi networks. Our team understands the common weaknesses that attackers exploit and has the skills needed to mitigate them effectively.
-
Expertise in Wireless Security: Our specialists are well-versed in the intricacies of Wi‑Fi networks and their security challenges.
-
Non‑Disruptive Testing: We take every precaution to ensure our testing methods don’t disrupt your business operations, preventing downtime and service interruptions.
-
Actionable Reports: Our detailed, easy-to-understand reports provide practical remediation steps for each vulnerability, enabling you to strengthen your network’s defenses immediately.
By choosing Digitpol’s Wi‑Fi Remote Hacking Pentest, you’re taking the first step in ensuring your business is protected from external threats and vulnerabilities. Contact us today to get started with a comprehensive security assessment of your Wi‑Fi network.