Cybercrime
,
Endpoint Security
,
Fraud Management & Cybercrime
Fraudsters and APT Gangs Hit Remote Workers With Phishing, Spyware, Ransomware
Cybercrime groups and nation-state hacking gangs are continuing to exploit the COVID-19 pandemic to further their aims, U.K. and U.S. security agencies warn.
See Also: Role of Deception in the ‘New Normal’
“APT groups and cybercriminals are exploiting the COVID-19 pandemic as part of their cyber operations,” Britain’s National Cyber Security Center and the U.S. Cybersecurity Infrastructure and Security Agency warn in a joint alert issued Wednesday, adding that they’re working with law enforcement agencies and the private sector to try to disrupt these attacks.
“Malicious cyber actors are adjusting their tactics to exploit the COVID-19 pandemic, and the NCSC is working round the clock with its partners to respond,” says Paul Chichester, director of operations at the NCSC (see: Coronavirus Cybercrime Victims: Please Come Forward).
“We urge everyone to remain vigilant to these threats, be on the lookout for suspicious emails and look to trusted sources for information and updates regarding COVID-19,” says Bryan Ware, CISA’s assistant director for cybersecurity. “We are all in this together and collectively we can help defend against these threats.”
Both agencies say they have not seen overall levels of cybercrime increasing. But they are seeing an increased use of COVID-19 themes via phishing emails and efforts to distribute malware, including via bogus apps that purport to offer information about the disease. And they predict that “the frequency and severity of COVID-19-related cyberattacks will increase over the coming weeks and months.”
Agendas Unchanged
APT groups – meaning hacking teams aligned to or run by nation-states – have been using lures and attacks with a COVID-19 theme as part of information operations, espionage and potential sabotage efforts, law enforcement officials say, while cybercriminals have been wielding malware, and especially ransomware, in their quest for illicit profits.
Both APT groups and cybercrime gangs have also been registering en masse domain names with a coronavirus connection, often to use in phishing campaigns, the NCSC and CISA warn.
Hackers Hunt Remote Workforces
With the COVID-19 pandemic leading many governments to instruct nonessential workers to stay at home, leading to a surge in remote workers, attackers have retooled to attempt to exploit this larger – and potentially less well-safeguarded – population (see: NASA: At-Home Workers Targeted by Hackers).
Earlier this week, the FBI warned that it’s seen a surge in business email compromise – aka CEO fraud – schemes that have a COVID-19 theme (see: FBI: COVID-19-Themed Business Email Compromise Scams Surge).
Beyond BEC schemes, many attackers have been probing for known vulnerabilities in VPN gateways and remote-access tools. “The NCSC and CISA have observed actors scanning for publicly known vulnerabilities in Citrix … and [we] continue to investigate multiple instances of this vulnerability’s exploitation,” the agencies say in their joint alert. The Citrix vulnerability (CVE-2019-19781) and its exploitation has been widely reported online since early January 2020.”
In January, both agencies issued alerts to all Citrix users to patch the flaw, which was first disclosed last December (see: Citrix Releases First Patches to Fix Severe Vulnerability).
Last October, U.S. and U.K. security and intelligence agencies issued a similar alert for users of Pulse Secure, Fortinet and Palo Alto products, warning that months after patches had been released to fix easily exploitable flaws in remote tools, many organizations had yet to apply the security updates, and that the flaws were being actively exploited by cybercriminals and nation-state attackers (see: NSA Is Latest Intelligence Agency to Sound VPN Patch Alarm).
Remote Desktop Protocol Use Increases
“The surge in home working has also led to an increase in the use of Microsoft’s remote desk protocol,” according to the joint NCSC and CISA alert. “Attacks on unsecured RDP endpoints – i.e. exposed to the internet – are widely reported online.”
On March 30, for example, cybersecurity firm Reposify reported that it had counted 4.7 million internet-exposed RDPs, noting that on some days, the number of such RDPs increased by 127 percent.
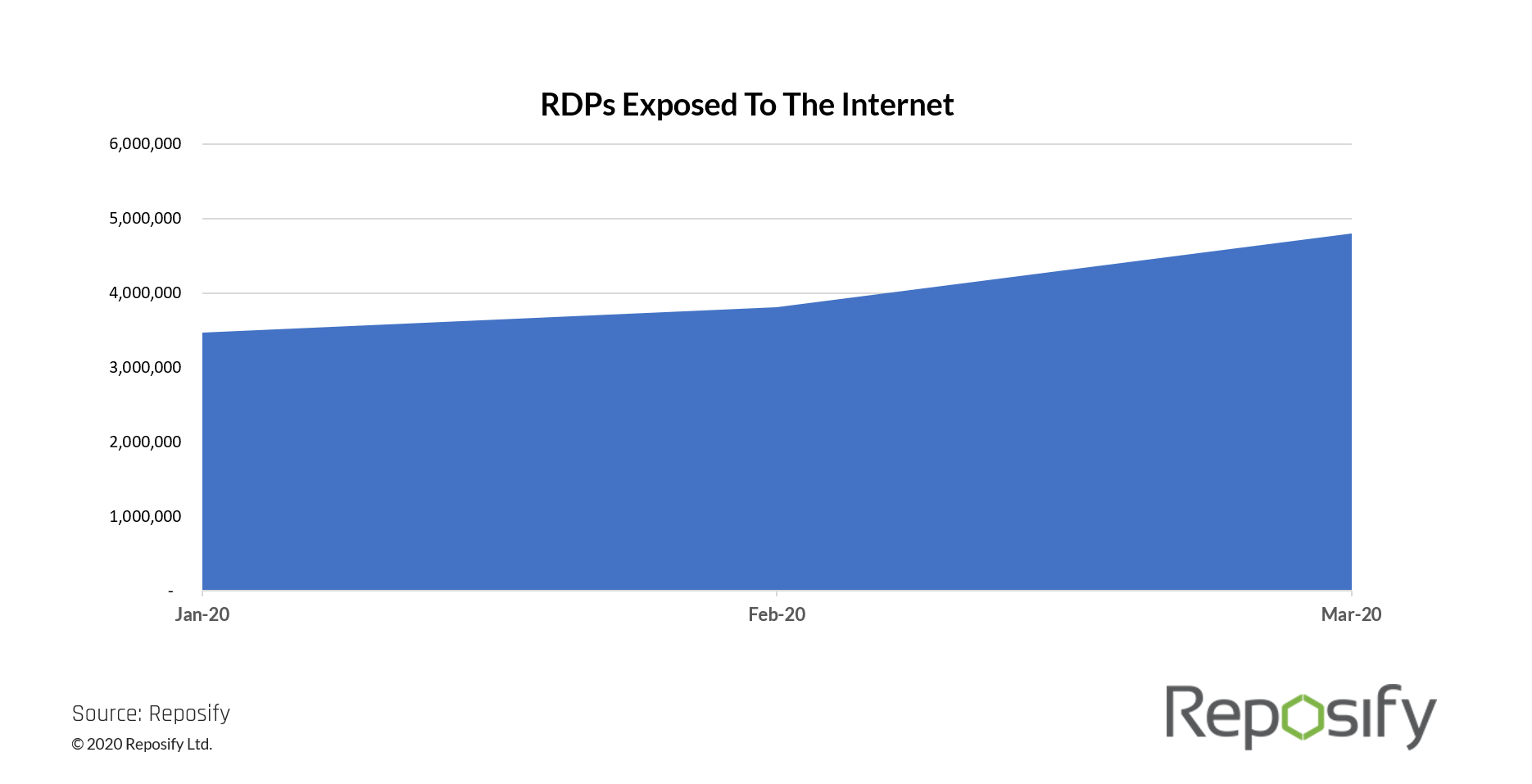
“The increase in RDP use could potentially make IT systems, without the right security measures in place, more vulnerable to attack,” the NCSC and CISA say in their joint alert (see: Is COVID-19 Driving a Surge in Unsafe Remote Connectivity?).
Many security experts expect attacks targeting work-from-home employees to continue to increase. “We predict an increase in the number of cyberattacks on unprotected home networks used by employees who have switched to remote work,” says Aleksandr Kalinin, head of the CERT-GIB computer emergency response team at Singapore-based security firm Group-IB. “A single employee who opens a malicious file from an undetected phishing email could jeopardize the whole company’s operations.”
Computer security teams must lock down work-from-home remote environments as quickly as possible, beginning by requiring two-factor authentication for accessing all email accounts and VPNs, he says, adding that “people should remain particularly vigilant now that most people are working from home due to the pandemic.”
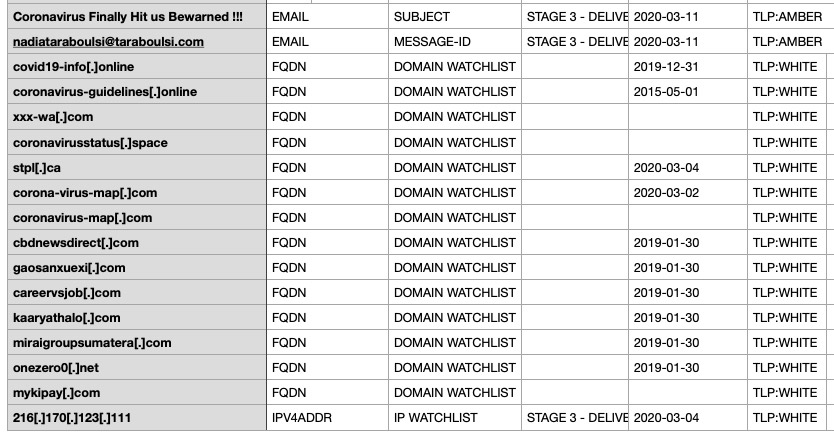
To help organizations better block attacks with a COVID-19 theme, the NCSC and CISA have published an extensive – albeit non-exhaustive – list of indicators of compromise, including domain names and IP addresses that have been tied to attacks or which appear to be suspicious or malicious.
‘Capitalizing on Fear’
Many attackers have been repurposing their existing efforts to try to take advantage of COVID-19 for the simple reason that people are scared – and fear leads to a decline in rational behavior.
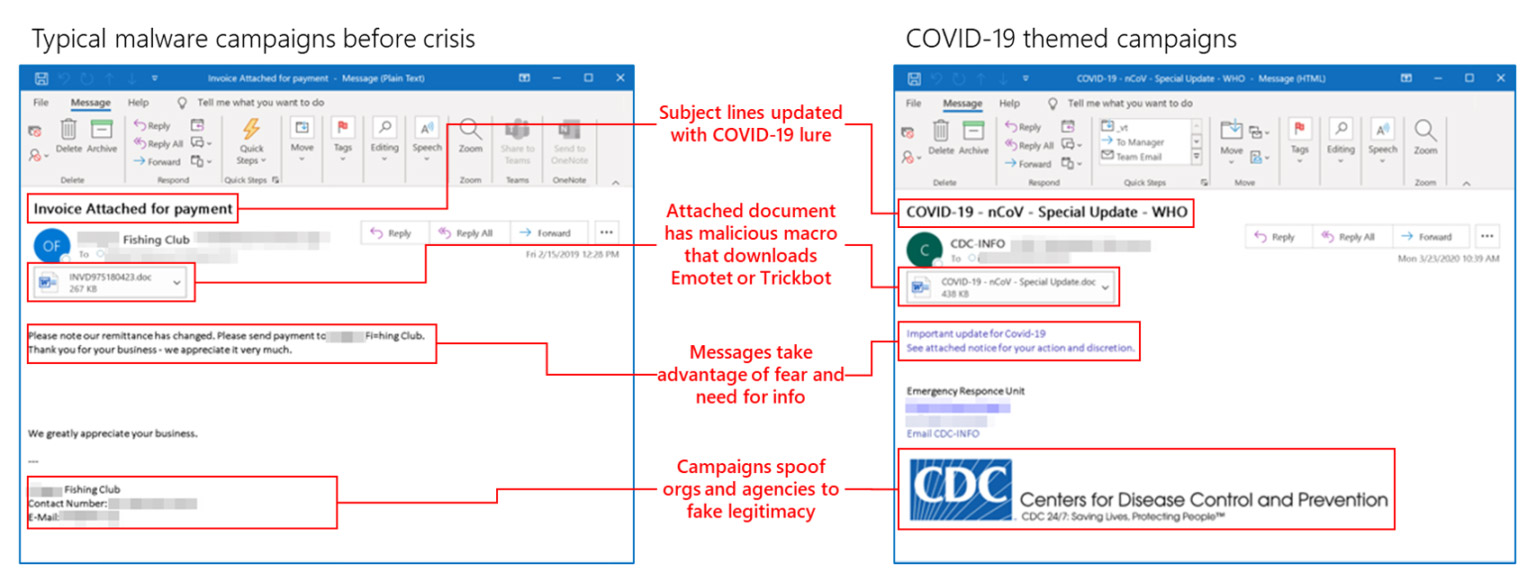
“Attackers don’t suddenly have more resources they’re diverting towards tricking users; instead they’re pivoting their existing infrastructure, like ransomware, phishing, and other malware delivery tools, to include COVID-19 keywords that get us to click,” says Rob Lefferts, vice president of Microsoft 365 Security, in a blog post.
“It’s overwhelming and attackers know it,” he adds. “They know many are clicking without looking because stress levels are high, and they’re taking advantage of that. That’s why we’re seeing an increase in the success of phishing and social engineering attacks.”

Of the thousands of email phishing campaigns that Microsoft says it tracks daily, about 60,000 are now tapping malicious attachments or malicious URLs that have a COVID-19 theme. While that might sound large, it only represents about 2 percent of the daily attacks Microsoft sees, thus reinforcing the assertion that “the overall volume of threats is not increasing but attackers are shifting their techniques to capitalize on fear,” Lefferts says.
Other security firms also report that coronavirus lures remain a relatively small part of the attack landscape. Group-IB says that from Feb. 13 to April 1, “phishing emails exploiting coronavirus panic accounted for about 5 percent of all malicious emails” that it detected. “This relatively small percentage can partly be explained by the fact that not all cybercriminals are capitalizing on coronavirus fears.”
Meanwhile, demand for some services appears to have declined. Group-IB says it’s found more than 500 posts to cybercrime forums that offer users “coronavirus discounts and promotional codes on DDoS, spamming and other services to stimulate demand.”
Malware Retools for COVID-19
Some attackers have also retooled their malware to take advantage of the pandemic.
For example, attackers wielding Trickbot and Emotet malware have been “very active and rebranding their lures to take advantage of the outbreak,” Microsoft’s Lefferts says. “We have observed 76 threat variants to date globally using COVID-19-themed lures.”
Group-IB says that of the campaigns it’s been tracking from Feb. 13 to April 1, about one-third of COVID-19 phishing messages pushed backdoors that provide remote access to attackers, while 4 percent of messages led to ransomware.
But the vast majority of these phishing campaigns – 65 percent – pushed spyware, and most often AgentTesla, Netwire and LokiBot strains. “With some minor differences, all these malware samples are designed to collect personal and financial data,” Group-IB says. “They can retrieve user credentials from browsers, mail clients and file transfer protocol clients, capture screenshots, and secretly track user behavior and send it to cybercriminals’ command-and-control servers.”
Top Targets: Healthcare, Finance, Education
As the joint NCSC and CISA alert makes clear, such attacks seem set to increase, and numerous security experts have been sounding the same warning.
Microsoft reports that attacks with a COVID-19 theme are already widespread, although China, the U.S. and Russia are so far hardest hit. “Every country in the world has seen at least one COVID-19-themed attack,” Lefferts says. “The volume of successful attacks in outbreak-hit countries is increasing, as fear and the desire for information grows.”
Christiaan Beek and Raj Samani, respectively lead scientist and chief scientist at security firm McAfee, write in a blog post: “The use of COVID-19 as a lure does not appear to show any sign of slowing down, indeed there are more campaigns being regularly identified. COVID-19 related threats are on the rise, from phishing emails name-dropping the disease to malware named after popular video conferencing services.”
Given the importance of healthcare – and its supply chains – in responding to COVID-19, it’s unfortunate that the sector appears to now be attackers’ top target.
“The volume of threats related to COVID-19 has been significant, with lures used in all manner of attacks,” McAfee’s Beek and Samani say. “Tracking these campaigns reveals the most targeted sector is healthcare, followed by finance and then education.”
Some ransomware gangs had promised to stand down their attacks against the healthcare sector, but this has not come to pass (see: No COVID-19 Respite: Ransomware Keeps Pummeling Healthcare).
“The attacks are as prevalent as ever,” says Bill Siegel, CEO of ransomware incident response firm Coveware. “There has been no abatement, empathy or free decryptor granted by cybercriminals.”
[ad_2]
Source link
Is your business effected by Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Contact Digitpol’s hotlines or respond to us online.
Digitpol is available 24/7.
Email: info@digitpol.com
Europe +31558448040
UK +44 20 8089 9944
ASIA +85239733884


You must be logged in to post a comment.