Penetration Testing of RF Networks — The Hacking Van
Mobile Penetration Testing of RF Networks — The Hacking Van
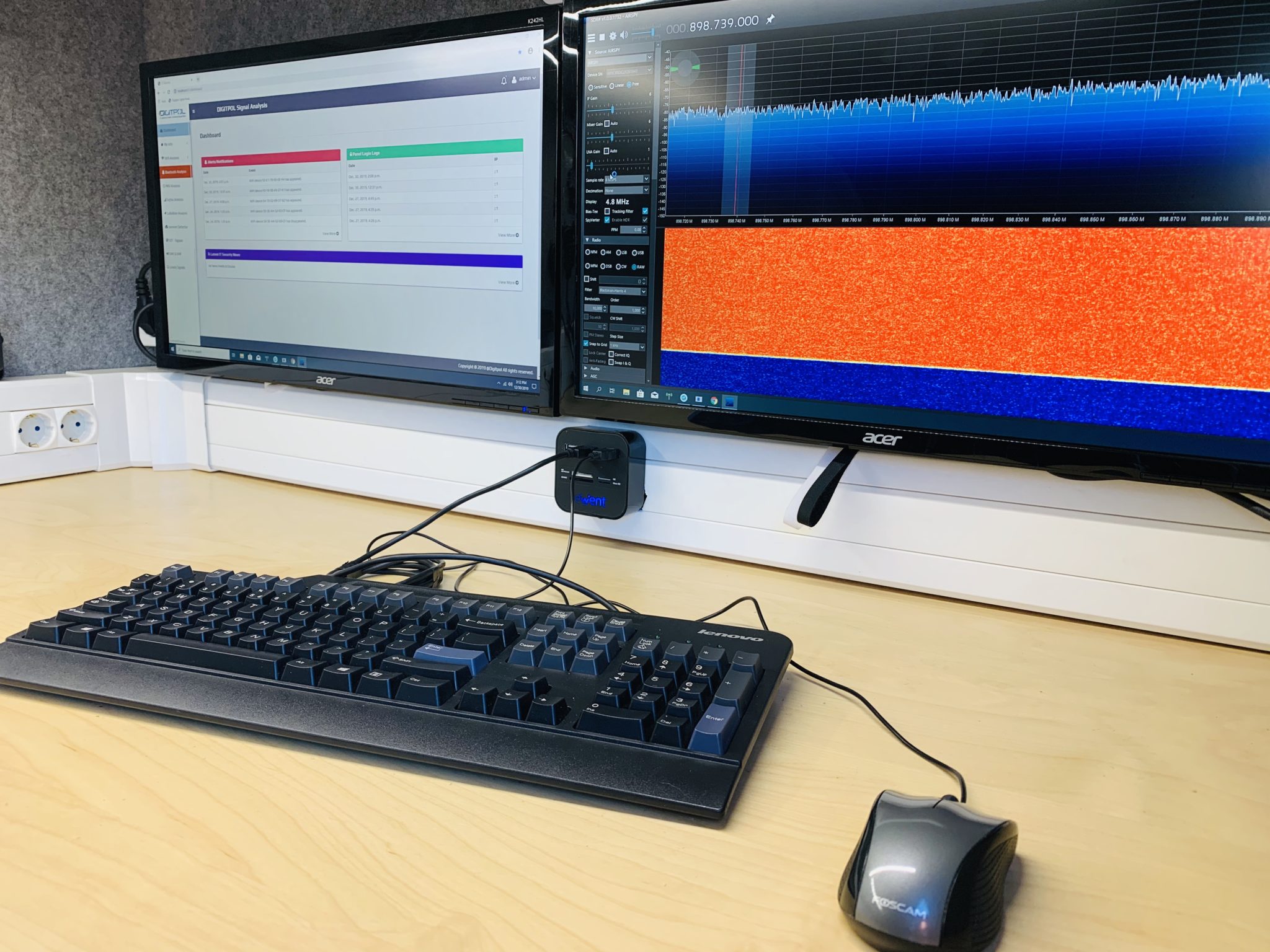
Digitpol’s mobile lab — “The Hacking Van” — brings advanced wireless and RF security testing directly to the field. Our fully equipped mobile unit performs remote field work including digital forensics, over‑the‑air RF testing, and wireless penetration testing, enabling us to evaluate your wireless defenses without ever entering your premises or having physical access to your internal systems. The goal of a mobile test is to simulate real‑world attackers who target RF and wireless networks from outside a facility, revealing weaknesses that could be exploited remotely and providing clear, prioritized steps to fix them.
We focus on the unique risks presented by wireless and RF environments. Typical testing covers the resilience of NFC, RFID, UHF, VHF, Wi‑Fi, Zigbee, 315 MHz, 433 MHz, 868 MHz, or 915 MHz, WirelessHART, ISA100 and other radio systems to remote attacks, the security of wireless management interfaces and cloud consoles, the effectiveness of guest and device segregation, and the potential for unauthorized over‑the‑air access. All assessments are performed with safety and non‑disruptive techniques by default; any intrusive or on‑site radio activities are only undertaken with explicit client approval and a signed Rules of Engagement.
Our process begins with scoping and authorization to ensure legal and operational safeguards are in place. The mobile team then performs discovery and non‑intrusive enumeration of externally reachable wireless assets, followed by a controlled assessment to identify configuration flaws, exposed management endpoints, and risky cloud integrations. When permitted, we demonstrate impact with safe, read‑only proofs of concept and document each finding in detail, including the business risk and step‑by‑step remediation guidance.
Certification Process
Upon successful completion of the Mobile Penetration Test, we’ll issue a Completion Certificate confirming that the test was conducted according to agreed-upon terms. If any vulnerabilities are discovered during the assessment, we will work with your team to guide the necessary fixes. Once the vulnerabilities are addressed, we will certify the fixed vulnerabilities with an updated certificate, ensuring that they are no longer exploitable.
By choosing Digitpol’s RF Remote Hacking Pentest, you’re taking the first step in ensuring your business is protected from external threats and vulnerabilities. Contact us today to get started with a comprehensive security assessment of your wireless network.
What We Test
Our service is usually carryout outside your business without providing us with any details, only the permission to test, we aim to test in a real life hacking scenario. We begin by assessing key components of your Wi‑Fi network and its connection to the cloud. Our testing focuses on several critical areas:
-
Public Wi‑Fi Management Interfaces: We identify any exposed cloud portals, controller access points, or SSH/HTTPS interfaces that may be accessible remotely by attackers.
-
Guest Network Segmentation: We test the security boundary between your public Wi‑Fi and internal systems to ensure proper isolation, preventing guests from bypassing network restrictions.
-
Authentication & Encryption: Our team reviews your over the air authentication methods (such as WPA2, WPA3, and 802.1X) to ensure they’re securely configured to prevent unauthorized access.
-
Cloud Vendor Accounts: We assess whether your cloud management consoles are adequately protected with strong access controls, including multi-factor authentication (MFA).
-
Lateral Movement Potential: If vulnerabilities are discovered, we demonstrate how an attacker might move laterally into your internal systems, always keeping safety and caution at the forefront.
- Protected Wifi Networks: Once we have tested open networks, we will then start to gain access to protected wireless networks.
How It Works
Our pentesting process follows a systematic approach designed to ensure thorough, effective, and non‑disruptive testing:
-
Scoping & Authorization: We start by discussing your network and confirming the scope of the test. We then ensure that all necessary permissions are in place through a signed Rules of Engagement document before testing begins.
-
Discovery & Enumeration: We identify publicly available assets, such as public IPs, cloud services, and Wi‑Fi infrastructure, to determine what’s exposed to potential attackers.
-
Vulnerability Assessment: Our team analyzes the configuration of your Wi‑Fi networks, guest network access points, and cloud systems for misconfigurations or flaws that could be exploited.
-
Controlled Exploitation: Using safe, non‑disruptive techniques, we simulate attacks to demonstrate how vulnerabilities can be exploited — typically showing proof-of-concept attacks like read-only configuration access or lateral movement.
-
Reporting & Remediation: After the test, we provide a comprehensive technical report, including detailed findings, risk analysis, and clear, prioritized remediation steps. We’ll also schedule a debrief to review the results and help guide next steps.
The wireless RF bands we will look to test.
-
Wi‑Fi (client networks, cameras, APs) — primarily in the 2.4 GHz and 5 GHz bands; we may also use 6 GHz (Wi‑Fi 6E).
-
Bluetooth / BLE (asset tags, phones, scanners, beacons) — 2.4 GHz (Bluetooth Low Energy).
-
Zigbee / Thread / Matter (IoT sensors, building automation) — 2.4 GHz.
-
Proprietary warehouse radios & wireless handheld scanners — 2.4 GHz, 900 MHz (regional), or other ISM bands depending on vendor.
-
RFID systems (inventory, gate/toll readers)
-
HF/NFC (13.56 MHz) for some short‑range tags/antennas.
-
UHF RFID (about 860–960 MHz worldwide, region‑dependent) for long‑range pallet/tag readers and toll/transponder systems.
-
-
LoRa / Sigfox / LPWAN (long‑range sensors, asset trackers) — LoRaWAN commonly sits in sub‑GHz ISM bands (e.g., ~868 MHz EU / ~915 MHz)
-
Vehicle telematics / cellular modems (truck communications, GPS, fleet management) — cellular bands across multiple frequencies (2G/3G/4G/5G bands vary by carrier and region); GPS/GNSS signals around ~1.2–1.6 GHz (e.g., GPS L1 ~1575 MHz).
-
Proprietary remote controls (gates, forklifts, garage doors, key fobs) — often in sub‑GHz ISM bands such as 315 MHz, 433 MHz, 868 MHz, or 915 MHz
-
Industrial wireless protocols / OT radios — WirelessHART, ISA100, or vendor wireless control links (often in 2.4 GHz or sub‑GHz bands).
-
Bluetooth‑based location systems / UWB (ultra wideband) for high‑accuracy positioning — UWB occupies wide swaths (GHz‑level) but is specialized and less common; UWB is used for precision locating, this needs to be encrypted by default.
-
Security cameras and video links — may be wired, Wi‑Fi, or use proprietary wireless links (2.4/5 GHz or licensed bands in some cases).
-
Short‑range low frequency systems (access control, proximity readers) — low‑frequency access badges/readers (125 kHz or 13.56 MHz) for doors and gates.